ALK Cyberhacks
Was your Alaska Airlines account compromised?
We are aggregating reports to demonstrate the true scale of this security failure to regulators and the media. If your miles were stolen, please help us build the case.
Disclaimer: Based upon the findings I made researching Alaska Air Group (ALK)’s spate of account hackings, I now have a short position on the company and stand to profit from a decline in ALK’s share price. Everything that follows is sourced from SEC filings, public social media posts and other public information.
Your Miles Were Stolen. Alaska Airlines Blamed You. Then Changed the Terms So They Can Take Them Back
Alaska Airlines hacks show a remarkable uniformity. I became intrigued when I first read a victim’s account back in August.
They were all last minute, business class, long haul flights on a partner airline with notifications somehow silenced. No diversions to gift cards, or Alaska-owned flights.
Then it was chance that dictated whether a member happened to log into their account before the flight had taken place as to whether the illicit traveller got away with the swindle.
The aftermath is also testament to the almost admirable adherence to process at Alaska:
The victim must call in (no online assistance for this matter).
The CSR makes the victim prove they are not a fraudster... reporting a fraud(!), so ID is demanded over unencrypted email.
The CSR then makes a show of Alaska’s benevolence by restoring the stolen miles. If the flight has not yet been flown, the CSR often advises the victim that the restoration would not happen if it had been flown.
A finger-wagging is given to the victim, and they are sternly told that this restoration will not happen a second time.
The victim is then told, in delicate terms of course, that their account is now permanently downgraded and they no longer are permitted to book award travel online like other members.
The victim must then create a verbal PIN. (which hopefully they commit to memory and do not recklessly write down or store online...).
The victim is told the full consequences of their account being hacked. Future award bookings must be preceded by calling a phone line open 6 days a week, during office hours.
When they get through and give the correct PIN, the their account functionality is restored for one hour only, during which they may book award travel like other members.
The sanctions on the victim’s accounts do not expire.
Back then, three things made no sense to me at all:
If there was an official policy to deal with these hacks, they must be very frequent, yet it seems such an obvious thing to prevent. Never mind two-factor authentication (2FA). How about preventing people the member doesn’t appear to know, from taking last-minute one-way flights, from far-away places?
The PIN detail makes no sense at all. First, sending more personal information to an account already compromised seems ill-advised. And I cannot think of a more archaic patch than a verbally given PIN. Most of all, the compromised password is changed. The only logical purpose of the PIN is if you believe the victim cannot be trusted to protect their new password and their downgraded functionality penalty is merited by their previous actions.
These illicit travellers are crazy to risk so much for a more comfortable bedding arrangement. The chances of discovery are immense, and they will be entering the most surveilled and secure environment, under their real name, with no idea if the ruse has been rumbled. The risk seemed wildly disproportionate to the benefits. This is what really bothered me. They must have some re-assurance that the odds are far better than I would imagine.
It bothered me so much that I looked for and found some more.
What I Found
What really struck me was the uniformity of the threads where someone would announce in terror that they had been hacked. The commenters always included several commentators damning the slow implementation of two-factor authentication. The customer service representatives often confirmed that 2FA was imminent, as recounted here ten months ago.
However a couple of things started to make me annoyed.
1. The amount of opprobrium placed upon the victim over their presumed moronic password habits. Most were civil and gave a general rejoinder for everyone to change their passwords and not reuse them. Others, however, were downright vitriolic towards the victim:
“You had a crazy simple basic password that was easy to guess or reset. I’m sick of taking the slack for people who aren’t careful online.” (archive)
2. How grateful and praiseworthy the victims were for superb customer service in replenishing these miles. The PIN limitation on their account was worth it to keep them safe. It was clear they felt that perhaps their password was to blame. That they were at fault. And that Alaska kindly let them off. This inspired gratitude rather than recognition that this PIN clearly demonstrated Alaska’s cybersecurity was weak.
So I went and found every single one I could.
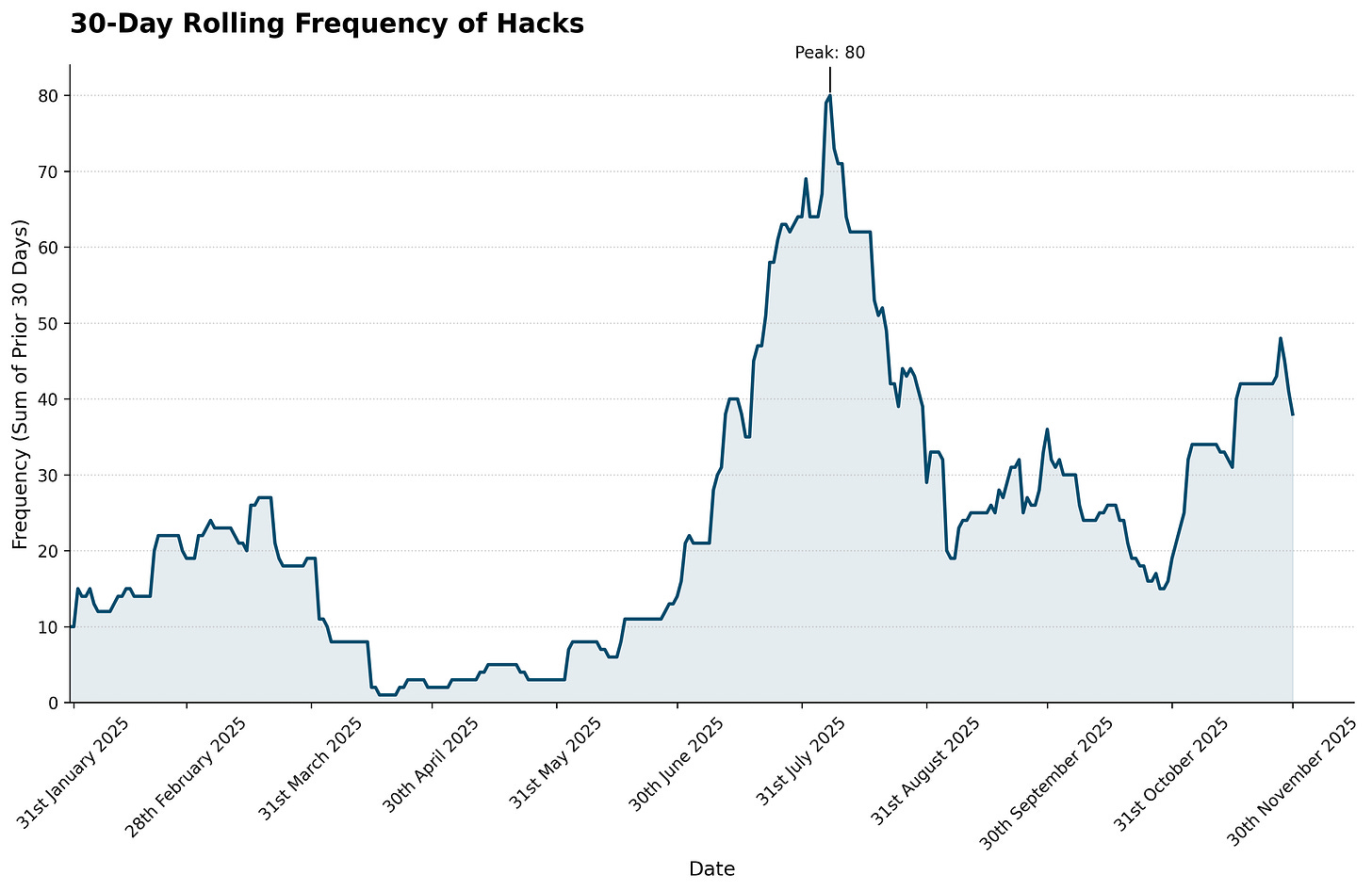
265 Documented Hacks
You can peruse them all here.
I drew a line at the end of November and found 265 separate hacks, averaging 218,000 miles per hack. You can see the peaks and troughs of reporting in this chart:
24 Times Higher Than All Other Airlines Combined
Now mileage thefts have been part of travel for some years, so it seemed worthwhile to compare Alaska’s record with the other major airlines. Results of my scientifically designed test were unexpected.
When you put the other airlines together, Alaska’s reporting rate is 24 times the combined total of the other airlines. This isn’t an airline problem. This is an Alaska problem.
Alaska: 80 reports from 60,000 subreddit members = 13.3 per 10,000 members
Southwest: 18 reports from 89,000 members = 2.02 per 10,000 members
American: 12 reports from 113,000 members = 1.06 per 10,000 members
Delta: 11 reports from 352,000 members = 0.31 per 10,000 members
United: 0 reports from 176,000 members = 0.00 per 10,000 members
And if we think about the blame put onto the victims, for that to be merited, one must posit that Alaska customers are 24 times more stupid with their passwords, or Alaska is 24 times weaker in cyber defences.
The Victim Punishment
In this context, when you start to look at the victims’ stories, they’re horrible. Of the 37 people who reported hold times - of course a very biased segment - the average was 100 minutes. Manifestly the victims, for no fault of their own, were being punished by this process.
A process, of course, with no logical underpinning because if the fault of the theft was an erroneous password and the password is changed, then that is no longer a vector where the account can be compromised - unless you now imply that the victim is too incompetent to be responsible for a password again. There can be no other meaning.
And Yet The Password Is No Defence At All
This user saw his miles being stolen, changed his password, gave up on the wait time, and came back to find he’d been robbed again.
These users were robbed despite having a PIN already in place.
Several victims explicitly stated they used unique, strong passwords generated by password managers.
One was a database security professional - precisely the sort of person who would notice poor security hygiene in their own practices.
Well, you can read them yourself. My personal favourite is the Titanium member (the highest status tier) being warned that he was under consideration for prosecution if it turned out to be him that was behind the theft.
Even the financial details were shocking. It seems if the hacker also got to use your credit card on file in your account to pay taxes and fees for these flights, Alaska would not offer any redress for that. Victims must take it up with their credit card company, which, if you think about it, is remarkable because if the credit card company agrees that this was a fraudulent charge, they will take it back from Alaska. So really, Alaska is just saying they refuse to take any responsibility for this.
Why Aren’t The Travellers Being Arrested?
Of the 265 documented cases, 56 said they contacted Alaska before the flights departed. Alaska had passenger names, itineraries, booking confirmations, departure times. Of those cases where origins were identified, 39% were in the USA - no jurisdictional complications.
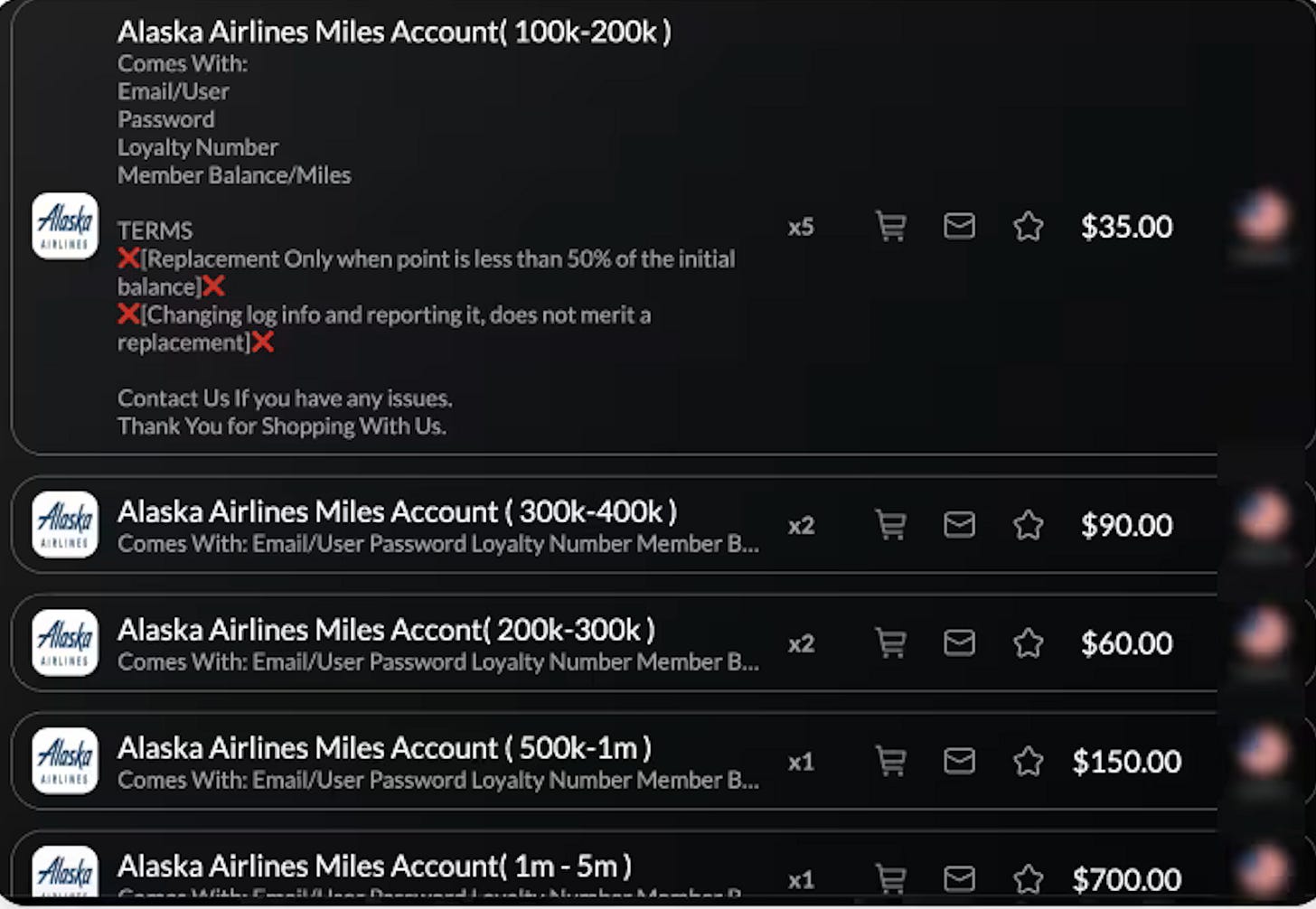
I found no record of arrests, detentions, or refusals of boarding. The dark web pricing tells the story: one-way long-haul business class for $35. China to London in a Q-Suite on Qatar where you get your own door - for thirty dollars.
Pricing can only be that low because demand is satiated whilst supply is abundant with almost no marginal costs.
We are talking China to London in a Q-Suite on Qatar where you get your own door… for $30!
Pricing can only be that low because Demand is satiated whilst Supply is abundant with almost no marginal costs.
The Scale of Thefts
Which brings us to the question of scale: how many hacks are going on? Alaska’s subreddit has 60,000 members, and of course you have the lurkers who pass by without being a member.
But this one blew my mind: the US Card Forum (a Chinese-language website for American residents who are looking to be canny with the points on their cards and maximise their mileage) had 33 victims on a website that has 12,000 weekly visitors.
Because when you think about it, how many people post? How many people originate posts? How many people post about this when you can reliably be patronised by commentators and perhaps receive a little spin of abuse? And of course you’ve already been remediated so there’s no imperative to complain. And of course you might feel a bit embarrassed as though it’s your fault.
Providence may have bestowed icebergs upon humanity solely so today we could use that metaphor in describing 265 hacks - they must be just the tip.
Help bring visibility to the scale of the problem. Individual complaints are easily dismissed, but a collective dataset is hard to ignore. We are tracking the total miles stolen and the timeline of these breaches.
The Scale of the Breach
We must look beyond the victims who lost miles. Not many members have hundreds of thousands of miles sitting in their accounts. Most accounts belong to occasional travellers or have been long forgotten.
Consider the mathematics. If only 5% of hacks result in public reports - a conservative estimate - then 265 documented cases implies 5,300 total thefts. But hackers cannot identify high-value targets without looking. If only one in twenty accounts contains enough miles to be worth stealing, hackers must have accessed over 100,000 accounts to find their 5,300 victims.
That’s a breach affecting nearly 1% of Alaska’s entire 12 million member base.
If these breaches were truly due to poor password hygiene - members reusing credentials from other compromised sites - we’d expect roughly 300 credential stuffing attempts per day to yield this outcome. The actual number is almost certainly far higher, which makes the “weak password” explanation completely implausible. These accounts are being accessed through a different vector entirely.
Moreover, if accounts are being accessed at a scale necessary to support this many thefts, then the personal data of the entire loyalty programme membership may be insecure and possibly exposed.
The Technical Evidence
The technical chaos is not theoretical. Random users stumble into it regularly.
A Hacker News user logged into their Alaska account and was randomly granted full access to other customers’ records: names, confirmation numbers, flight details, contact information, with complete ability to cancel or modify bookings. Refreshing the page served up a different stranger’s account. They reported the vulnerability to Alaska. The response? 3,000 miles (worth roughly $30) and a request to log out and back in.
Four months later, the same user experienced the identical vulnerability. Nobody had fixed it.
This wasn’t a sophisticated hacker exploiting a zero-day vulnerability. This was an ordinary user who simply logged in and found Alaska’s systems couldn’t distinguish one customer session from another.
But it’s not just one user. Others report similar experiences:
One member received flight confirmation emails for four people they don’t know.
Another found someone else’s reservation appearing in their profile.
A third received refund confirmation for something they didn’t request.
Yet another described the “bizarre experience” of seeing other passengers’ details when they logged in.
These are not hackers. These are random customers stumbling into data they should never see, discovering that Alaska’s systems cannot reliably distinguish one user session from another. One can only imagine what a sophisticated malevolent actor could do with these vulnerabilities.
And it’s expensive for Alaska. The fraudulent passenger flies on a partner airline that expects payment. Then Alaska restores the miles to the victim. Alaska pays twice for the same redemption.
Alaska Finally Fights Back
Despite coverage by the Seattle Times, Fox13 Seattle, and Kiro7, Alaska’s only substantive response came from the head of their loyalty programme who, in a Reddit Q&A, acknowledged that ‘fraud attempts are getting worse almost daily’ - hardly a reassuring defence for the lack of meaningful cybersecurity measures.
Alaska let their actions do the talking as they took clear and decisive action to combat the the fraudulent mile thefts that must surely be beginning to bleed serious amounts of cash. Discreetly, they directly addressed the financial effects upon them and their most valued customers:
“Alaska Airlines may deny, revoke, or adjust Atmos Rewards points, status points, awards, or benefits at any time, including after they have been posted or redeemed, if determined to have been granted in error, including due to system or partner issues, regardless of member fault.”
They silently added a defensive legal firewall to the loyalty programme terms and conditions (archive).
At the expense of not only future victims, but historical ones too. This extra paragraph appeared sometime after the 11th September version where it was absent. Indeed this was the only non-cosmetic change. Removed of interjections, the new term directly says:
“Alaska may revoke points, including after they have been redeemed if, due to system issues, regardless of member fault”
Alaska awarded themselves, without any appeal mechanism, the authority to revoke points, even if redeemed many years ago, if they cite an issue with the system they own and control. The value of members’ miles tumbles if you have no ownership rights.
Worse, you now carry a non-zero probability that “system issues” of the past will cause long-spent miles to be revoked and a liability to emerge. I am being absurd, but so is that condition.
What benign reason exists for Alaska to add language specifically permitting them to revoke miles “due to system or partner issues, regardless of member fault”?
Alaska appears to have deliberately changed their terms to unambiguously remove any obligation to restore miles stolen from victims due to Alaska’s own security failures.
The Hawaiian Airlines Victims
Former Hawaiian Airlines members - who experienced no documented hacks before the merger - were dragooned into this chaos:
“I had Hawaiians mileage acct for a very long time no issues. Since ‘Atmos’ came along, I have been hacked twice for 750 thousand miles.”
The merger was conditional on Alaska’s CEO personally signing an undertaking to the Department of Transport that Alaska would not “impose new limits on access” to members’ miles. The PIN restrictions and terms change appear to violate that binding commitment.
The End State
Now I would be incandescent with rage if I was one of these victims. Clearly, by any measure, Alaska’s most lucrative, valuable, and loyal customers are being grossly mistreated.
When your miles were stolen due to uniquely Alaska’s security failures:
You were blamed
Your account was restricted
You were told restoration was a courtesy
You were warned you would not be helped again
You must now telephone and wait for hours to use what you earned - at one stroke your propensity to use your miles plunged and any economist would agree that those miles became instantly less valuable, with that drop in value to you manifestly being reallocated to Alaska Air Group
Alaska changed the terms so they can revoke your miles at any time for system issues regardless of your fault
Meanwhile:
Alaska has not implemented two-factor authentication
Alaska cannot stop last-minute bookings by strangers to distant geographies
Alaska apparently does not pursue prosecution of fraudulent travellers
The hacks continue unabated
The new platform launched in August changed nothing
November 2025 saw 38 documented hacks
Your miles are not safe. Your personal information is not safe. Your ability to use what you earned has been permanently degraded. And Alaska has granted itself the unilateral authority to revoke your miles for their own failures.
The technical infrastructure is compromised. The customer response is punitive. The terms have been changed retroactively. The scale is in the thousands. And there is no end in sight.
Nobody could look at these accounts and have any doubt that by a matter of rigidly upheld policy, Alaska has been degrading the value of the miles of their most loyal customers when it must be known internally that their IT systems are not only compromised, but are so badly infiltrated that they cannot stop these hacks and these data breaches.
In the last four quarters, Alaska has found $800M for share buybacks, but no budget could be found to protect their members’ data and miles. These breaches have been unacknowledged and used to assault Alaska’s best customers by having the value of their miles degraded as the price of Alaska’s reprehensible cybersecurity and more than that, the victims who are unquestionably led to believe it was their fault.
Even those who wear both belts and braces could never refute the possibility of their password being compromised. Indeed if exemplary password hygiene was in place, you could only conclude that your entire life - accounts, messages, emails - must be compromised and you had no idea what had happened. Think of the emotional turmoil being inflicted there, all out of expediency for the airline to whom you had given your custom, and your loyalty.
Alaska found $800M to buy back shares over the previous year, but couldn’t spare a dime to lock the back door. They aren’t protecting your miles because they don’t think they are yours. They think they are theirs.
If Your Account Was Compromised Too, Bring Light To The Issue
Full documentation, methodology, and financial analysis available in the complete report and databook.