Alaska Airlines: Where the Top Customers Get Punished
For 4 years, Alaska Airline’s members’ accounts have been stolen from via exactly the same vulnerability.
The average theft when stated, is 225,000 miles. Thefts have been as high as a million. Thieves are only interested in high balances, and high balances are only held by Alaska Airline’s most loyal, and most lucrative, customers.
The policy response has been to not only shift blame onto the victims, but permanently restrict the functionality of their accounts.
The response can be summed up well by an account by a Titanium level member who was told:
“if we find out this was you. We will peruse [sic] prosecution.”
I cannot recall another example of a firm blaming their cyber breaches on their customers.
I also cannot recall a cyber breach remaining open for 4 years.
See below all the verifiable facts that showcase this astonishing corporate policy
A Timeline of Systemic Failure (2022-2026)
FACT ONE: April 2022 - The Pattern Emerges
Date: 3 April 2022
Source: FlyerTalk - “My Mileage Plan Account Was Hacked”
A FlyerTalk user reported their account had been drained of 140,000 miles to book Qatar Airways flights. The attack pattern was already sophisticated:
Email notifications were completely suppressed (hacker changed email, then changed it back)
The PNR was not accessible to the legitimate account holder
Award tickets booked for international travel in someone else’s name
Date: 4 April 2022 (Next Day)
Source: Same thread
Another victim emerged with an identical experience. Alaska’s response policy was already established:
“They reset my account, put the miles back in, then said I needed to add a pincode next time or they would not refund the issue in the future.“
The victim-blaming framework was already operational. The “one-time courtesy” language. The PIN lock solution that shifts operational burden to customers. The implicit threat that future thefts would not be remediated.
All of this existed in April 2022.
FACT TWO: Present Day - Nothing Has Changed
Date: January 2026
Source: Recent Reddit victim testimonial
Four years later, members’ accounts are being hacked in exactly the same way. A recent example:
“Happened to me. Several individuals from the Middle East flew into Texas on 500,000 of my points. They were able to use my Alaska credit card attached to my account to pay for in-flight food and WiFi—plus seat upgrades.
Alaska only refunded my miles under the condition that my account is now locked down by them and I have to call customer service to get it unlocked with a code every single time I want to book.
They refused to refund the several thousand dollars that was charged to my card (which itself was NOT compromised—they only could charge to it through the app) and told me to dispute the charges with the credit card company.”
The attack characteristics remain unchanged:
Last-minute international premium cabin bookings
Notification suppression
Stored payment methods exploited
Victim bears the remediation cost
The airline’s response remains unchanged:
Miles restored as “one-time courtesy”
Permanent account restrictions imposed
Credit card charges declared customer’s problem
Zero operational improvements implemented
FACT THREE: Nearly 4 Years of Institutional Paralysis
Time Period: 3 April 2022 to 11 January 2026
In nearly four years, not a single element of these thefts has been closed off.
Consider what hasn’t been implemented:
✗ Two-factor authentication (2FA)
✗ Redemption email notifications sent to permanent email on file
✗ Geolocation-based anomaly detection
✗ Partner airline coordination to flag suspicious bookings
✗ Law enforcement cooperation protocols
✗ Session monitoring for account takeovers
✗ Temporary holds on large redemptions
✗ Saved payment method removal capability
Nothing.
Every airline peer has implemented basic controls. Alaska operates in 2026 with 2019 security architecture while under sustained, documented attack.
FACT FOUR: Media Coverage Has Been Extensive and Ignored
July 2025: Fox13 Seattle
Date: 23 July 2025
Source: “Hacked Alaska Airlines accounts cost flyers miles”
“Several Alaska Airlines customers are sounding the alarm this week after discovering their frequent flyer accounts were hacked—and their miles were stolen. Victims say hackers canceled their flights, drained their miles and resold them on third party sites.”
July 2025: KIRO 7 Seattle
Date: 1 August 2025
Source: “Alaska Airlines customers complain of possible hack after miles stolen from accounts”
“A growing number of customers with Alaska Airline miles are reporting their miles disappearing from their accounts after an apparent hack.”
November 2025: Seattle Times (Most Comprehensive)
Date: 28 November 2025
Source: “They were saving up Alaska Air miles. Then their accounts got drained”
The Seattle Times investigation documented:
Multiple victim testimonials with specific theft details
Expert commentary from Gary Leff (loyalty program specialist)
Industry-wide comparison showing Alaska’s unique vulnerability
Technical explanation of why loyalty accounts lack banking-level security
Alaska’s failure to implement 2FA despite years of incidents
Alaska’s official response? Corporate boilerplate:
“Addressing the fraud and safeguarding our guests’ hard-earned points is a priority for us.”
Note the word “priority.” Not “accomplished.” Not “resolved.” Not “prevented.” A “priority.”
This statement means nothing. It is designed to mean nothing.
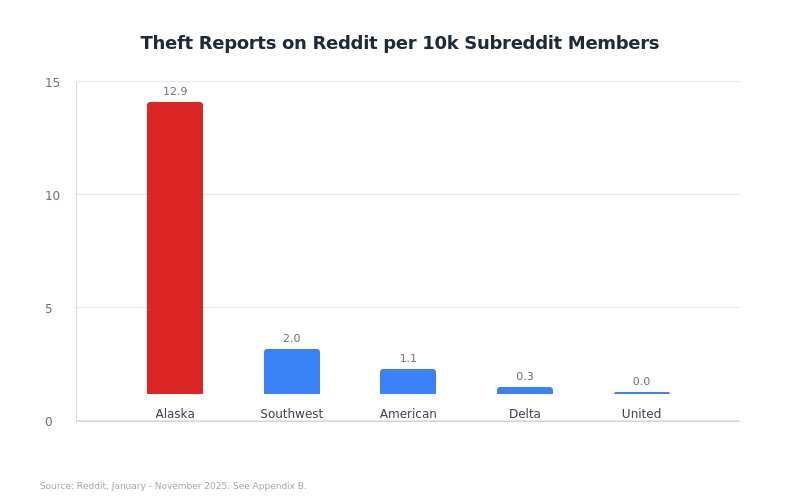
FACT FIVE: Peer Airlines Have Implemented Basic Security
Comparison (January-November 2025):
Source: Controlled Reddit methodology, identical search parameters, same time period
When weighted by community size: Alaska experiences account compromises at a rate over 20 times higher than airlines that have implemented basic 2FA/MFA controls.
This is not a user password problem. This is an architectural security failure.
FACT SIX: Management Acknowledges the Problem But Takes No Action
7 October 2025: Reddit AMA
Source: Thrifty Traveler coverage of Brett Catlin AMA
Brett Catlin, Alaska’s Vice President of Loyalty, Alliances, and Sales, stated publicly:
“We know this is a major pain point, and honestly, fraud attempts are getting worse almost daily. It’s something we take very seriously, and it has visibility all the way up to our CEO.”
On MFA implementation:
“Multi-factor authentication (MFA) is coming soon. It’s not just on the roadmap—it’s actively in the works because we know how critical this is for protecting accounts and peace of mind.”
Critical Context:
This statement was made in October 2025
As of January 2026, MFA/2FA remains not implemented
The VP’s own Ultimate Rewards points were once stolen (he admitted this in the AMA)
Management admits:
The problem is worsening daily
The CEO is aware
A solution is “actively in the works”
Yet after 4 years of documented thefts, the most basic security control remains absent.
FACT SEVEN: Alaska Silently Changed Terms to Eliminate Liability
Dates: Between 11 September 2025 and November 2025
Source: Alaska Airlines Atmos Rewards Terms and Conditions (current) vs. Web Archive 11 Sept 2025
What Was Added (New Paragraph):
“Alaska Airlines may deny, revoke, or adjust Atmos Rewards points, status points, awards, or benefits at any time, including after they have been posted or redeemed, if determined to have been granted in error, including due to system or partner issues, regardless of member fault.“
Analysis:
This clause did not exist before September 2025. It was added silently, with no announcement, during the period of escalating thefts.
Key phrases:
“including after they have been posted or redeemed” = Alaska can claw back miles even after the victim has already used their “one-time courtesy” restoration
“due to system or partner issues” = Alaska’s own system failures are no longer their responsibility
“regardless of member fault” = Being a blameless victim is no longer sufficient grounds for reimbursement
This is a legal firewall constructed while the attacks accelerate. It specifically addresses the scenario where Alaska’s systems fail, customers are victimized, and Alaska wants the ability to deny reimbursement.
Why would you add this clause unless you anticipated needing to invoke it?
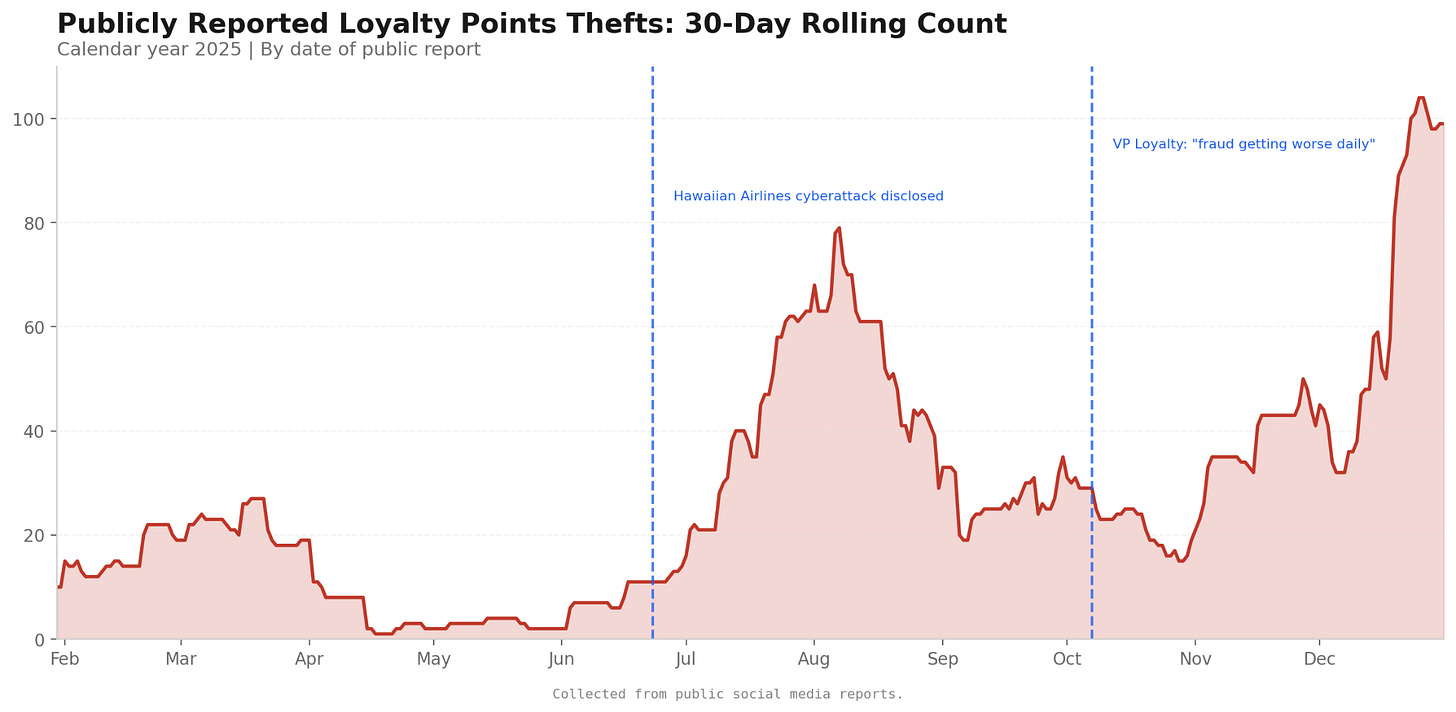
FACT EIGHT: The Rate of Thefts Is Accelerating, Not Stabilizing
Source: noseyparker.org analysis of 370 documented 2025 thefts
The rolling 30-day average exhibits clear step-changes, not random noise. This pattern is inconsistent with isolated incidents or stable background fraud rates.
It is consistent with:
Platform-level vulnerabilities being discovered and exploited
Growing awareness among criminal networks
Information sharing among fraudsters
Or actual system compromise
FACT NINE: Victims Report Sophisticated Platform-Level Attacks
Evidence of Non-Credential-Stuffing Attacks:
Example 1: Same-Day Repeat Compromise
Source: Reddit archive
Account hacked twice in one day. Password changed between incidents. Both thefts successful.
If this were credential stuffing, the password change would prevent the second attack. It didn’t.
Example 2: PIN Lock Bypass
Source: Reddit archive
Account compromised despite Alaska’s mandatory PIN lock already in place.
The PIN lock is Alaska’s supposed security solution. It is being bypassed.
Example 3: HackerNews Session Hijacking Report
Source: HackerNews archive
User reported logging in and randomly being granted access to other customers’ accounts. Four months later, the vulnerability persisted.
This is not user error. This is a session management failure at the platform level.
The common thread is not weak passwords. The common thread is Alaska.
FACT TEN: Alaska Refuses to Cooperate with Law Enforcement
Example 1: Houston In-Flight Notification
Date: 12 July 2025
Source: Facebook - Award Travel by Roame
“Someone hacked my Alaska mileage and currently enroute from Dubai to Houston via Qatar airways business class. How do I report this or even better get them arrested if possible. They’re not anticipated to land until after 4pm?”
Context:
Victim discovered theft while fraudulent passenger in transit
Destination: Houston (major US port of entry with CBP presence)
Multiple hours between notification and landing
Clear opportunity for law enforcement coordination at arrival gate
Observed outcome: No indication Alaska coordinated with CBP or law enforcement.
Example 2: CSR Direct Discouragement
Date: 14 May 2025
Source: Reddit archive
Victim: “I asked if I should report to authorities”
CSR Response: “told me not to even bother“
Alaska customer service representatives are actively discouraging victims from contacting law enforcement.
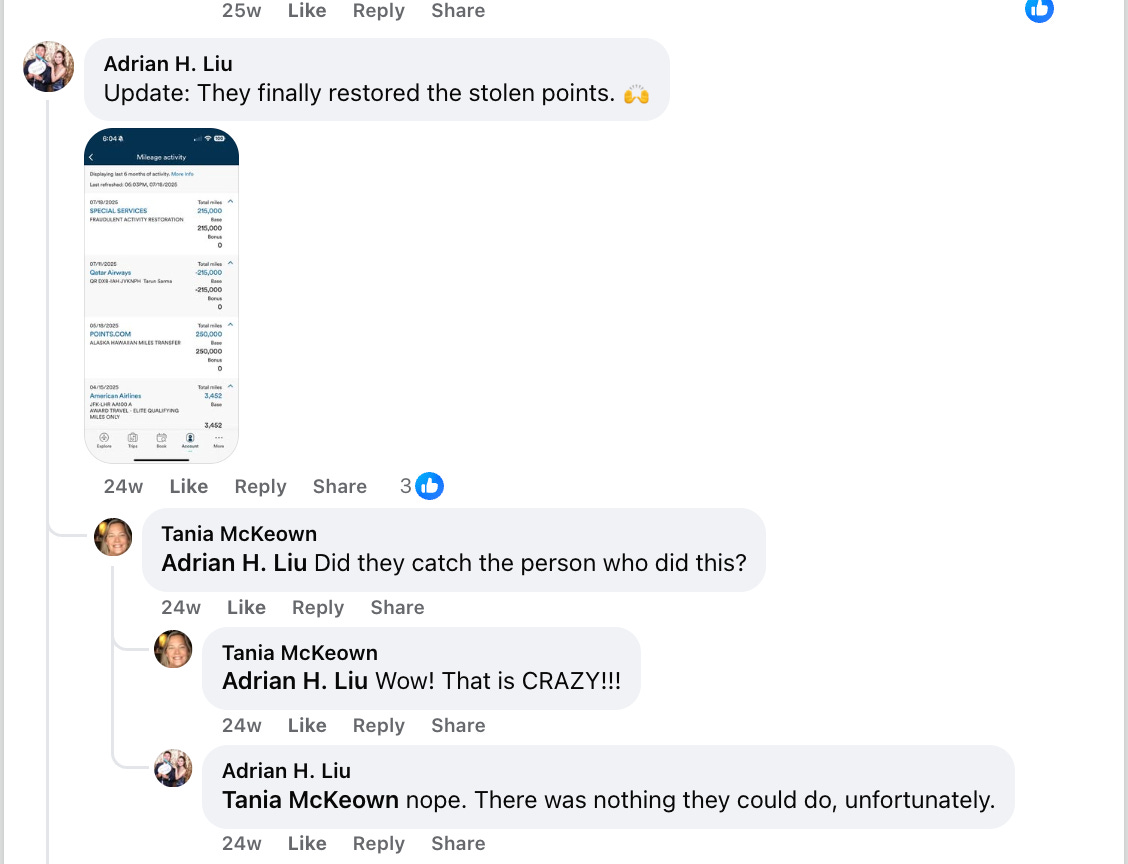
Example 3: Instagram Evidence Ignored
Date: 26 November 2025
Source: Seattle Times interview
“Three years ago 160,000 miles were stolen from my Alaska Airlines mileage account. I noticed it about 2 hours before the flight was to depart Doha Qatar. I had the travelers name, passport number etc. I called Alaska and alerted them but they would do nothing. I found the perp on Instagram and saw pictures of him and his lady toasting their travels with champagne! Alaska did nothing...”
Victim provided:
Advance notice (2 hours pre-departure)
Full passenger identity and passport number
Post-travel photographic evidence
Alaska’s response: Nothing.
Independent Validation: Alaska AG Letter
Date: 30 December 2025
Source: Alaska Attorney General Stephen Cox letter to Alaska Airlines
The Alaska Attorney General independently called out Alaska Airlines’ institutional non-cooperation with law enforcement.
This is not speculation from victims. This is official documentation from a state law enforcement authority.
FACT ELEVEN: Victims Must Now Call During Business Hours With Indeterminate Wait Times
After being victimized by Alaska’s system failures, customers face:
Permanent Restrictions:
Can no longer book award travel online like other members
Must call dedicated phone line open 6 days/week during business hours only
Must provide verbal PIN to unlock account
Account unlocked for 1 hour only before re-locking
This restriction applies for life
Wait Time Data (December 2025 Reddit reports):
Sample of victims who reported wait times in the last week:
One CSR admitted to handling “3-5 of these per day” (14 May 2025).
The Perverse Economics:
Alaska’s platform failure creates a liability. Alaska’s solution is to convert that liability into a permanent tax on the victim’s time. The miles remain on the books, but their utility has been materially impaired for precisely those members whose lifetime value justifies the co-brand economics.
High-balance accounts are targeted because they’re worth stealing. Post-theft, those same high-value customers are permanently downgraded to telephone-only access with 90-minute hold times.
This is not a security solution. This is liability shifting.
FACT TWELVE: Credit Card Charges Go Unreimbursed
Source: Multiple victim testimonials
When thieves use a stored credit card attached to the account (not the card itself being compromised, but accessed through the hacked Alaska account):
Alaska’s position:
Miles will be restored (as “one-time courtesy”)
Credit card charges are the victim’s problem
Victim told to “dispute it with your credit card company”
The Double Standard:
If the victim disputes with their credit card company, the credit card company will dispute the charge with Alaska (the merchant). Alaska may or may not contest this.
But Alaska refuses to directly reimburse the victim for charges made through Alaska’s own compromised platform using the victim’s own stored payment method that the victim did not authorize.
This forces victims to either:
Eat the charges (can be thousands of dollars)
Open fraud disputes that damage their relationship with their credit card issuer
Spend additional time fighting Alaska through the credit card company’s dispute process
The platform failure is Alaska’s. The financial burden is the customer’s.
Analysis: There Is Only One Logical Conclusion
For nearly four years, from April 2022 through January 2026, Alaska Airlines has been unable to stop account thefts despite:
Extensive media coverage in their hometown market
VP of Loyalty public acknowledgment that “fraud attempts are getting worse almost daily”
CEO awareness of the problem
Multiple promises that 2FA/MFA is “actively in the works”
Peer airlines successfully implementing basic controls
370 documented cases in 2025 alone representing likely thousands of total victims
Documentation of institutional non-cooperation with law enforcement
Silent terms changes to eliminate future liability
Acceleration of theft rates through Q4 2025
Alaska Airlines’ IT systems are so compromised, brittle, or architecturally deficient that they are unable to implement even basic security controls without risking platform stability or operational integrity.
There is no other explanation that reconciles:
The sustained failure to implement MFA/2FA
The acceleration of thefts despite awareness at the CEO level
The victim-blaming response pattern that shifts cost to customers
The silent legal terms changes to eliminate reimbursement liability
The active discouragement of law enforcement cooperation
The 23.4× higher normalized theft rate compared to peers
If Alaska could fix this, they would have. The fact that they haven’t, after four years of documented attacks, suggests they can’t.
CLOSING NOTE
On 4 January 2026, a formal SEC whistleblower complaint was filed documenting:
The 10.40 sigma accounting anomaly in Q2 2025
The unexplained $180M excess loyalty liability creation
The $195M affinity receivables spike
The $120M non-current asset reclassification
The pattern of platform failures and customer restitution
The accounting anomaly and the cybersecurity failures are not separate issues. They are symptoms of the same underlying reality:
Alaska’s loyalty programme is not operating as a closed, fully controlled, auditable system.
When a system cannot enforce basic account security, it also cannot reliably govern issuance, redemption, and settlement flows.
The evidence presented in this document is not interpretation. It is documentation.
Every statement is sourced. Every date is verified. Every quote is preserved in archives.
The pattern has been consistent for 4 years..
And in that time, nothing has changed.
DISCLAIMER: The author holds a short position in Alaska Air Group (ALK) and stands to profit from a decline in the share price. This report represents analysis of publicly available information, including SEC filings, public financial data, and social media documentation. It constitutes opinion, not investment advice.