THE GAME IS UP AT $ALK
EXPOSING AN ASTONISHING 4-YEAR COVER-UP
A Simplified Summary
The Forensic Report (released 9 Jan)
The Addendum (released 26 Jan)
The Simplified Summary (here)
The earlier report posed taxing questions of Air Alaska Group management. The Addendum answers enough of them to bury them.
Below is a strident attempt to remove the evidentiary requirements of the other reports, and to freely share the fruits of the Nosey Parker’s investigation into Alaska Air Group, just as they came to the investigator.
DISCLAIMER: The author holds a short position in Alaska Air Group (ALK) and stands to profit from a decline in the share price. This supplementary addendum should be read in conjunction with the main report dated January 2026. It represents analysis of publicly available information and constitutes opinion, not investment advice.
The Core Finding
Alaska has known since 2022 that its loyalty platform suffers from a cyber vulnerability that goes far beyond password compromise
The key discoveries
370 cases of stolen air miles have been uncovered over 2025 (likely the tip of the iceberg).
Every case follows the same pattern: a consistent method of theft; a ALK strategy of victim blaming; an imposed PIN ‘solution’ that is entirely inconsistent with the supposed password breach.
A host of accounting anomalies and other irregularities have served to prevent investors and authorities from learning the true nature of the cyber breaches.
This Report
Earlier this month, the Nosey Parker released a report identifying a host of accounting anomalies and other irregularities at Alaska Air Group (ALK).
Concurrent with this release, is an addendum to that report. The investigation has now gone far enough that we no longer need answers from ALK, as those answers have been found independently.
This report sets out plainly what the other reports do forensically.
Was your Alaska Airlines account compromised?
We are aggregating reports to demonstrate the true scale of this security failure to regulators and the media. If your miles were stolen, please help us build the case.
Summary
The core finding is straightforward:
Alaska Air Group has known since at least 2022 that its loyalty platform suffers from a cyber vulnerability that goes far beyond password compromise.
Rather than disclose this to investors or fix the flaw, Alaska weaponised the victims, impugning them as a necessary step in implementing their ‘remedy’: the telephone PIN lock.
The telephone PIN lock, mystifying at first, proved vital in ALK’s attempts to prevent account thefts. It is also the smoking gun in this corporate cover-up.
The only logical function of imposing a PIN on customers is to conceal that their accounts were compromised not by errant passwords, but by session-level cyber breaches. ALK has been aware for 4 years that accounts have been accessed and drained without any password compromise.
What follows is the investigative path, right from its genesis, in the order in which discoveries were made. All compiled from public information.
And all instigated by the singular LinkedIn post of a stranger…
Act 1: The LinkedIn Spark
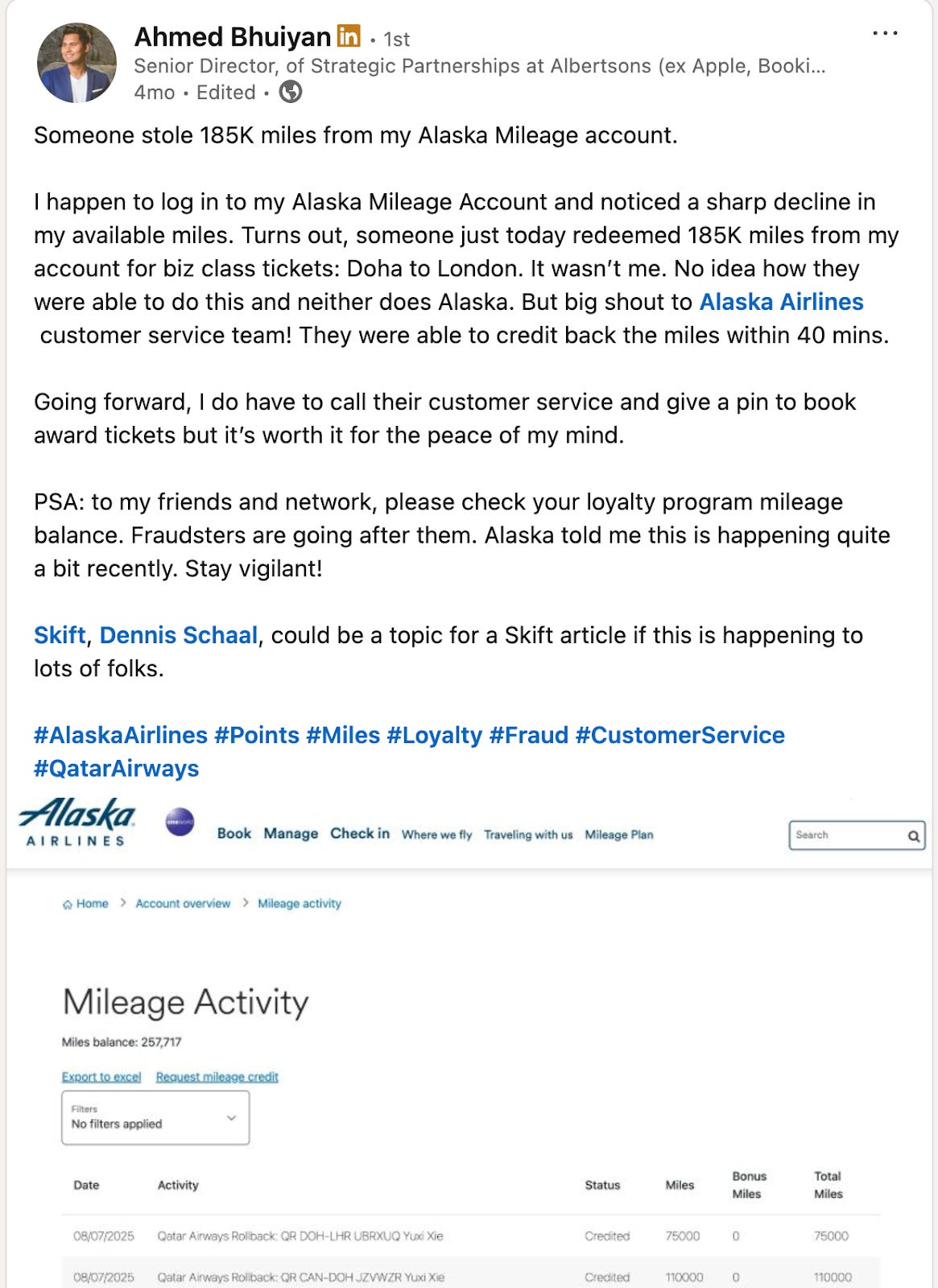
In August, the author saw a LinkedIn post about an Alaska Airlines member having their account drained of their loyalty points and subsequently replenished. Others responded to the post to announce similar experiences.
Three logical non-sequiters bothered the author enough to investigate:
Why can’t ALK block these clearly fraudulent bookings and stop the thefts?
What purpose could the mandatory telephone PIN booking forced upon the victim serve?
Why would the fraudulent traveller, Mr. Xie in this case, take the staggering risk of passing through secure environments under their real identity, for so little reward?
The questions were perplexing enough to launch an investigation.
Act 2: 2025 Thefts Gathered
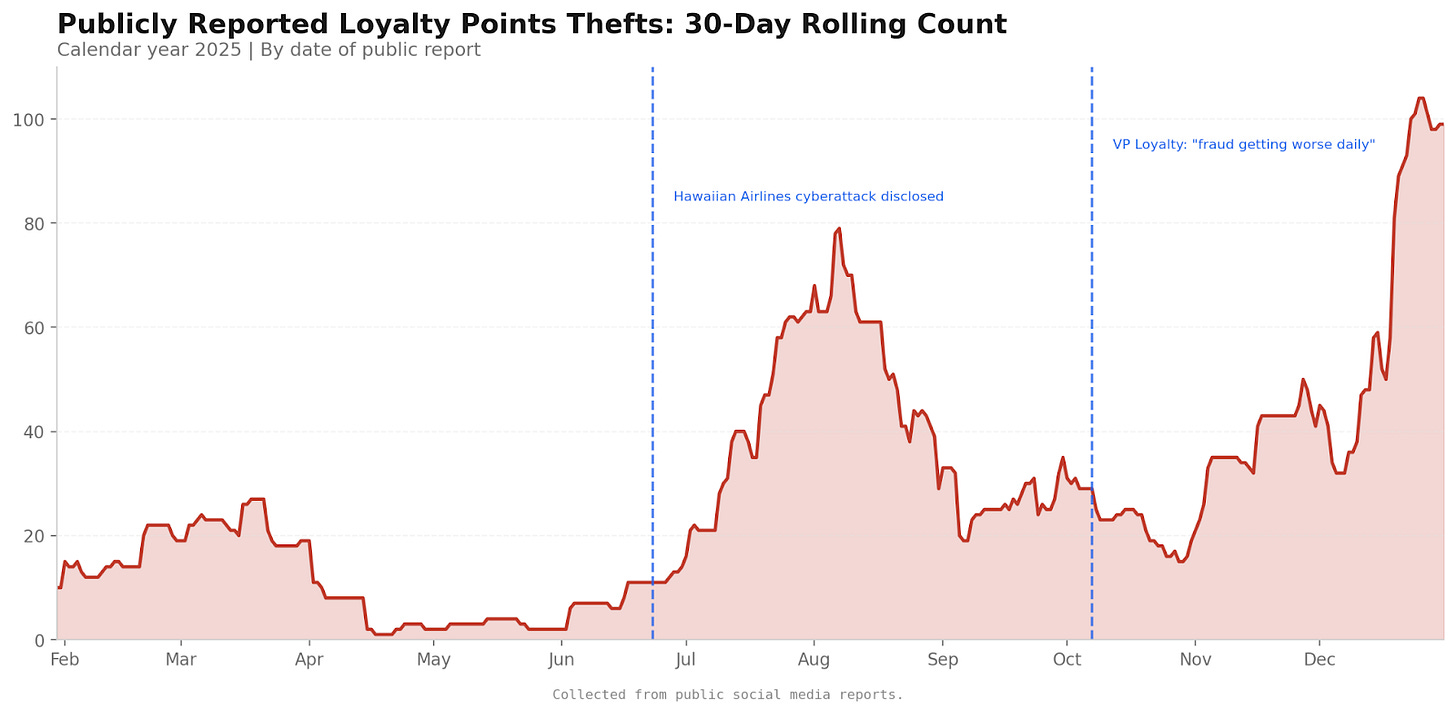
The investigation found 370 thefts from ALK loyalty programme members across 2025.
220 cases were found amongst two dedicated loyalty-point obsessive groups and one credit card point-maximising website, in Mandarin.
Alaska Airlines Reddit group: 62,000 members
Facebook group dedicated to Alaska Airlines loyalty points: 42,000 members
Aforementioned Chinese-language US Card Forum: 30,000 members
Act 3: Mode of Theft
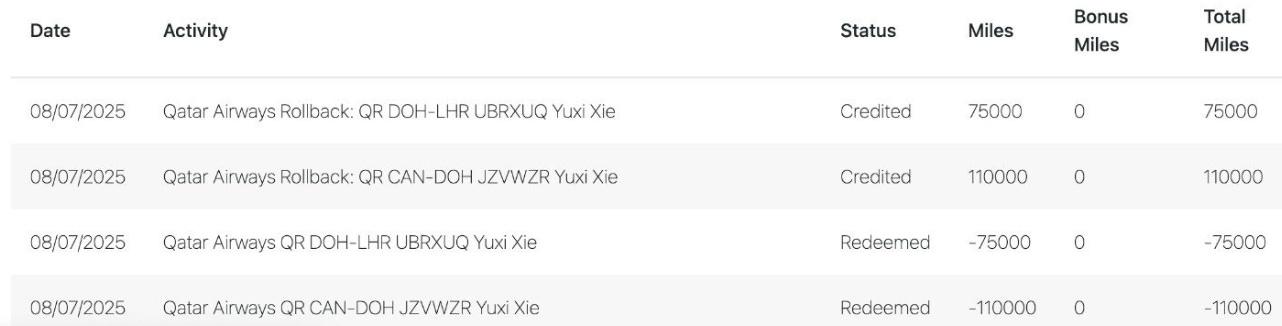
The thefts almost universally showed the same characteristics. Indeed the thefts have shown the same manner since 2022.
Accounts were compromised to book flights within a day or two of travel
Flights were booked not on ALK, but on a partner airline
Flights invariably had significant value. The average points theft when disclosed was 225,000.
The member’s notification email was changed to prevent them discovering member’s awareness of the booking.
Invariably, the theft was discovered by the victim reviewing their account, whether that be hours or months after the incident.
Act 4: ALK Response Policy
ALK’s responses to a theft were so consistent that they must undoubtedly be the product of a policy, also unchanged since 2022.
Victims were advised of the importance of protecting their passwords.
ALK reimburses the stolen points as a one-time courtesy. Victims advised a future theft would get no refund.
Any credit card charges made with the card on the account were not reimbursed and must be pursued elsewhere.
Victim exhortations for law enforcement involvement were dismissed and arguably, obstructed.
Victims are no longer able to book award travel online. They must speak to ALK, verbally relaying a PIN to unlock their award account for one hour, before it is closed again.
Act 5: The Industry Backdrop
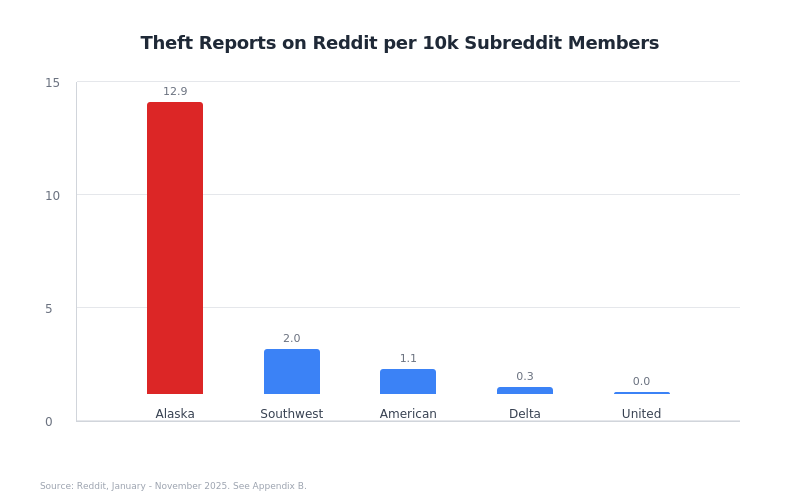
A study was performed to estimate the incidence of ALK thefts vs peer airlines. Though just a snap shot of the true issue, it gives an estimate of 23x thefts compared with other airlines, adjusting for airline size.
`
Act 6: Tip of an Iceberg
370 incidents were revealed for 2025. Logically, these must be the tip of an iceberg for the 12 million active loyalty programme members:
60% of reports came from fringe online communities representing roughly 1% of all members
ALK provides enough resolution to make a settled event. There is no incentive for victims to publicly clamour for redress
The proclivity for original posting and commenting is purported to be 1% and 9% respectively. Many victims, like the wider population, are not inclined to publicly post.
The actual number is not possible to ascertain from the 370 incidents. Anecdotal evidence of CSRs processing hacked accounts 3-5 times per day do little to define the scale. However it is inconceivable the total victim count is not a significant multiple of the 370
Act 7: SEC Filing Anomalies on Loyalty
The investigation turned to Alaska’s SEC filings. No mention of account thefts appeared. But the financial statements revealed something else.
Loyalty Accounting Primer
When an airline’s affinity partner (i.e. Bank of America) induces consumers to use their card for the Alaska loyalty points on offer, those points must be paid for. Upon issuance by Bank of America, they must then pay Alaska an agreed rate. Alaska, like all airlines, then divides that payment. The future cost of delivering on those loyalty points is precisely worked out, and that portion goes to loyalty issuance. It is a future liability to ALK. However any remainder can be taken as revenue, and indeed almost straight to profit.
What Happened in Q2 2025
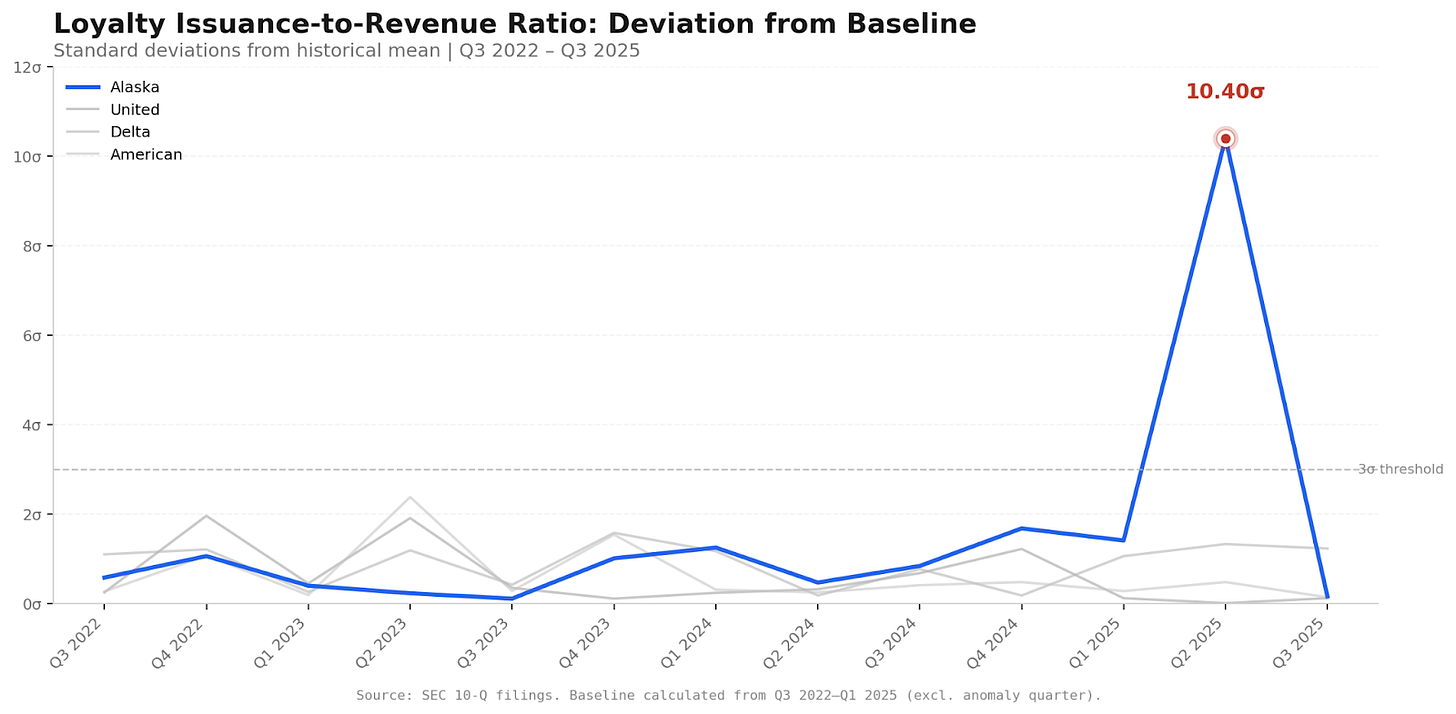
In the second quarter of 2025, Alaska created approximately $180 million of new loyalty liability. But the corresponding revenue did not appear.
The ratio of liability creation to revenue recognition deviated 10.4 standard deviations from Alaska’s historical baseline.
No peer airline showed anything comparable in the same period.
Following The Money
The delta of excess loyalty issuance was $180 million compared to the mean. What explained this large diversion from trusted and valuable loyalty programme economics?
The answer appeared in a different line item: ‘receivables due from affinity card partners’ (i.e. Bank of America). This balance, which historically fluctuated around $100 million, spiked to $306 million in Q2 2025.
By Q3, the receivables balance had subsided to $177 million. But the reduction was not matched by an increase in operating cash flow that would have been notable. Instead, $120 million migrated into Other Non-Current Assets.
The Disclosure Gap
Under US accounting standards, movements of this magnitude require explanation. A change in how loyalty economics are measured, a change in partner settlement terms, or a change in collectibility assumptions would each trigger specific disclosure requirements.
Alaska provided none.
The $180 million liability creation, the $195 million receivables spike, and the $120 million migration into non-current assets remain unexplained in the public filings.
The main report tests seventeen alternative explanations for these movements. Each fails on timing, magnitude, or disclosure requirements.
The loyalty issuance notable for having no matching revenue, now is not being paid for at all. Other Non-Current Assets by definition, are assets which will not release cash flows for at least 12 months. $120 million from that issuance now sits there.
Act 8: Disclosure Aversion
ALK has shown clear examples of aversion to clarity in their reporting.
The main report highlights how a re-statement in Q2 2025, of the balance of ‘receivables due from affinity card partners’ for Q4 2024, could not have been more obfuscating.
The Appendix B of the Addendum highlights another example relating to their recent court case with Virgin America.
In what amounts to a court decision, upheld on appeal, that ALK must pay $200 million to Virgin America, double the reported 2025 Net Income of $100 million. The existence of the lawsuit filed in 2019 is not acknowledged until Q3 2022, where it is dismissed as ‘without factual or legal merit’.
That phrase was repeated subsequently, despite the judgement going against ALK, right up until the final appeal decision also went against ALK.
ALK’s disclosures in both these matters have indisputably hindered investors’ understanding.
Indeed no CFO could say with earnestness, they had transparency in their hearts on those prior matters.
Once a firm has a shown a penchant for obfuscation in other matters, then that knowledge should be transferred to future matters by the discerning investor/.
Act 9: Scattered Spider Undisclosed
On 27th June 2025, an 8-K filing announced that ALK had been breached by a cyber attack.
Seven months later, investors can only speculate from the last comment on the subject three months ago. Q3 2025 10-Q gave an identical boilerplate commentary to all previous statements on the breach.:
“we do not believe the incident had, or is expected to have, a material impact on Hawaiian’s [Alaska Airlines’] business, results of operations, or financial condition. The investigation remains active and therefore we are unable to determine the full impact of the incident at this time.”
What Airlines Simultaneously Breached Disclosed
Qantas disclosed that six million member accounts were compromised and that ransom demands had been received. Executives were all held accountable for this penetration and had their remuneration docked. WestJet disclosed proportionally a similar loss.
Alaska has disclosed nothing beyond the statements above that admit nothing, disclose nothing, but deny nothing. Investors are left to forget, or to speculate.
The Correlation
The timing is notable. Documented loyalty theft reports accelerated sharply following the 23 June breach date.
Who Attacked
Cybersecurity researchers unanimously attributed the breach to Scattered Spider, an organised crime collective considered as sophisticated as some nation-state actors. The group was responsible for the 2023 MGM Resorts and Caesars Entertainment attacks, which cost over $100 million combined.
In July 2025, the FBI issued a formal alert on 1 July confirming the group had expanded into the aviation sector.
The CISA (Cybersecurity and Infrastructure Security Agency) advisory on Scattered Spider documents that one of the group’s attack vectors is “Steal Web Session Cookie(s).” This is precisely the vulnerability that a PIN-lock protocol would serve as a last resort defence against.
If Scattered Spider obtained session tokens from Alaska’s systems, the ongoing thefts would require no password compromise at all. The attackers would simply re-enter at will.
The Implicit Message
Alaska’s position to investors is that Scattered Spider breached Alaska, WestJet, and Qantas, but Alaska’s systems resisted. It is hard to fathom that Scattered Spider, who bow to nobody in notoriety, western state security services combine to combat, met their match in Alaska Airlines’s cyber defences. An organisation that has been shown that they apparently have been unable to change a line of code in four years.
The parsimonious disclosure on this topic is likely to have left a de facto message to inattentive investors in ALK, Scattered Spider met their match and came away with nothing.
The alternative conclusion, however, is also plausible: Alaska has disclosed nothing as a commercial choice.
Act 10: IT Backdrop
ALK has suffered severe flight disruptions due to IT breakdowns on 20th July, 23rd October and 29th October this year.
In response, ALK announced “a comprehensive audit of its technology systems” by Accenture on 31st October.
Act 11: Session Bleeding
Imagine logging into your bank account and finding yourself inside someone else’s account. Their name, their balance, their transaction history. You could transfer their money. They would never know you were there.
This is session bleeding. It occurs when a system fails to properly isolate user sessions, allowing one authenticated user to access another’s data.
Alaska Airlines users report this happening routinely.
The Evidence
This HackerNews post documents this exposure in detail:
“Alaska exposes other customers names, record locators, flight information, phone numbers emails, and probably more. I could have canceled or changed these people’s flights.”
The poster reported all to ALK. Four months later the poster noted nothing had been fixed.
These examples abound, such as this recent example from 22nd January 2026, where a user complains of repeatedly receiving other flyer’s confirmation details.
What This Reveals
Session bleeding and session hijacking are symptoms of the same underlying failure: Alaska’s systems cannot reliably distinguish one user from another.
If innocent users can inadvertently access strangers’ accounts, malicious actors can do so deliberately. The session architecture that permits bleeding is the same architecture that permits theft.
The HackerNews user could have cancelled strangers’ flights. The thieves documented in this report appear to have booked flights instead.
Act 12: The IT Revelations Underlying the Thefts
The technical flaws permitting the account thefts, unchanged since 2022, are indisputable:
The Bookings
A clear inability to put any fraud notification on last-minute, premium flight bookings, made on partner airlines, under a different identity to the member.
This shows ALK is completely architecturally blind when these fraudulent bookings occur. Alaska must have no way to view these bookings in real time, let alone prevent them.
The Notifications
Key to the success of the fraudulent traveller is the victim not being notified of the upcoming flight. The hackers fix this by simply changing the email address which receives the notification. In four years, any number of basic impediments to this, such as notifying the email address being retired, remain unimplemented.
This reveals Alaska’s complete technical paralysis. When technical debt becomes overwhelming, codebases become ossified as the slightest change in them risks catastrophic unforeseen calamities elsewhere in the business
There can be no other explanation for an alteration that appears so trivial to the outsider.
The Aftermath
In nearly all cases, the thefts are discovered by the victim. Often some months later. One must assume some are never noticed.
Yet if victim reporting is the method of discovery, then logically the scale of the thefts is only partially known to ALK. Knowing partially the level of fraudulent losses, yet not know the proportion, is no different from having no idea at all.
Yet, consider the simplicity of identifying these fraudulent flights within members accounts, once fully within your a modern database. A SQL query of moments to expose the suspicious flights of the past.
Either, ALK’s information systems are so utterly broken that even this cannot be achieved, or they have chosen not to. It is hard to weigh up which would be worse for their investors.
Act 13: Management Response
Despite being highlighted multiple times by different media throughout the year, there has never once been any acknowledgement beyond generic statements, that this issue even exists.
The cancellation of the Q3 2025 earnings call denied the opportunity for any questions on this issue. Then, on 4th December, CFO Shane Tackett relayed the early findings of Accenture’s comprehensive technology audit. Four weeks from announcement, the market’s hopes were low that definitive answers would be available. The market was not ready for Tackett:
“we don’t have a systemic architecture failure in our data or infrastructure which was good to hear.”
Indeed Tackett, as detailed in the Addendum report went on to relay Accenture’s findings, which appeared to be an IT architecture in rude health. The IT meltdowns he described as ‘flukes’ and if ALK were guilty of a weakness it was “pushing what we would call [sic] innovation or initiatives.“
A remarkable relaying of Accenture’s view when thery were commissioned clearly upon their announcement of conducting “a top-to-bottom review of Alaska’s technology environment.”
As without doubt. Without a single question mark, Alaska Airlines continues to see its members accounts drained through an ongoing security breach.
It can be inferred that Accenture must have blessed this report out with their own findings. How can Accenture have missed observing such a compromised, and indeed ossified, IT environment. The 370 victims in the database compiled by the Nosey Parker can be instantly validated for authenticity via hyperlink to their original location, and also to an archived one.
Irrefutably ALK have an ongoing systematic architectural failure.
Act 14: The Smoking Gun: A Four-Year Concealment
The evidence that password compromise cannot explain the hacked accounts is abundant.
None is clearer than this account from a victim hacked twice in a single day.
“Hacked Atmos account, TWICE in one day, even after changing password. How does that even happen?? Couldn’t get through to customer care, it was a 3+ hour hold time. Tried again this evening when I found the second hack and another person flying on my miles.”
A password change did not stop the second theft. The attacker returned within hours.
Session Hijacking: The Factor That Fits the Evidence
When a user logs in, their browser receives a session token, a digital credential that confirms their identity for subsequent requests. If an attacker obtains this token, they can access the account without knowing the password. Changing the password does not invalidate the stolen token.
This explains how accounts are compromised repeatedly despite password changes, and how victims who profess sophisticated password storage have been hacked.
There must be dozens of people within Alaska Airlines and possibly within Accenture who know this full well. The following proves ALK have known this for 4 years,.
The Proof in the PIN Lock
When a victim reports a hacked account to ALK, they are told that their account has been drained as their password has been compromised. The unmistakable subtext is laid out - the victim must be in some way to blame.
No matter your password hygiene, nobody can say with certainty that their password has not been compromised.
With the victim naturally fearing their loyalty points are lost, ALK then reveals they will restore the stolen points as a ‘one-time’ courtesy.
The victim is overwhelmed often. Observe the linkedin post where it all began. The accolades and praise heaped upon ALK by victims and onlookers alike is striking.
The victim is then told they are no longer permitted to book award travel online. For future bookings, they must instead phone ALK, and recite a PIN. This allows their account to be unlocked for online award bookings, for one hour, before being locked again.
Faced with such an act of benevolence, victims find themselves in no place to object to the sanction now placed on their account.
The Logic of the PIN Lock
The logic behind this security buffer is mystifying at first. The compromised password is now changed. Surely it cannot be that ALK has marked the victim as unreliable? Surely it cannot be a punishment for slapdash password protection?
No. There can be only one logical explanation that has driven this policy since 2022.
ALK can have no idea how the account was compromised. However, ALK knows that at least some accounts are being stolen via session hijacking.
If the victim’s account was accessed this way, then their account remains just as vulnerable after a password change.
In fact, there is a way of preventing this: unplug award travel booking from online access.
The telephone PIN unlock system does exactly this. There can be no other reason.
The direct implication is that ALK have known about an ongoing cyber breach since at least April 2022.
For 45+ months since, Alaska Airlines have been. systemastically blaming, and punishing their customers. Indeed hack victims invaribly only become so due to their large balances that show them to be Alaska’s most loyal and lucrative customers. Yet the existance of the telephone PIN unlock system is proof that hacks through session hijacking are not the fault of users failing to protect their passwords.
The wider implications of this unavoidable conclusion are seismic.
Act 15: The Implications
The most troubling aspect of this investigation is not what it uncovered – it is what Alaska itself cannot know.
Nearly all documented thefts were discovered by victims, not by Alaska. The company has no independent mechanism to detect compromised accounts or fraudulent redemptions until customers complain.
This means Alaska cannot answer basic questions about its own loyalty programme: How many accounts have been compromised? How many fraudulent redemptions have occurred? What is the true liability exposure?
The Tip of an Iceberg
The 370 documented thefts represent only those victims who noticed the loss and chose to speak publicly. The actual number is unknowable from outside the company. It is likely unknowable from inside as well.
For 45 months, Alaska has responded to each victim with the same script. The breach was your fault. Your password was compromised. We will restore your points as a one-time courtesy. Do not expect help again.
This was not negligence. It was a Machiavellian strategy. Blaming victims served two purposes: it deflected liability and prepared victims to accept the PIN lock without objection. Having been told they were responsible, victims were in no position to question why their accounts required permanent restriction.
Now Must Come The Reckoning
A loyalty programme that cannot verify its integrity cannot certify its liability balance. A $3.4 billion deferred revenue line item resting on a platform that detects fraud only when victims complain is not an auditable number. It is an estimate contaminated by an unmeasured error term.
An auditor presented with evidence that internal controls over redemption depend entirely on customer self-reporting faces a binary choice: qualify the opinion or explain why the control environment remains effective despite documented architectural failure.
A management team that attributed technology failures to “an abundance of innovation” and declared “no systemic architecture failure” weeks before this publication must now reconcile those statements with 370 documented thefts, session bleeding reported and unfixed, and a remediation protocol that proves awareness of session-level compromise.
A corporate policy of refusing law enforcement cooperation, must now be defended to regulators who will ask why criminals were permitted to board aircraft on stolen credentials without consequence.
None of this requires external action to crystallise. The evidence is assembled. The questions are framed. The documentation is public and archived.
The only remaining variable is time.
Act 16: The LinkedIn Mysteries Answered
Only now can the Nosey Parker finally rest, and those three LinkedIn questions that vexed him so much, that the cacoethes of this investigation could not be resisted.
Mystery One: Why can’t ALK block these clearly fraudulent bookings and stop these thefts?
Because its systems cannot see them. The architecture that processes award redemptions has no fraud detection capability
Mystery Two: What purpose could the mandatory telephone PIN booking forced upon the victim serve?
The PIN lock’s purpose is vital. Victim’s accounts are liable to be drained repeatedly, unless the accounts have their ability to book award travel removed entirely. The PIN lock allows them to be unplugged.
Mystery Three: Why would the fraudulent traveller take on such staggering risks?
Because Alaska does not pursue them. The company declines to coordinate with law enforcement, discourages victims from filing reports, and refuses to share passenger details with authorities. The criminals have learned there is no risk.
ABOUT THE AUTHOR
Tommy Caton was co-founder, Chief Revenue Officer, and Chief Financial Officer of travel data analytics firm AirDNA from 2015 to 2022. He holds an MBA in finance from the Kellogg School of Management (Northwestern University) and worked for four years in KPMG’s Corporate Finance division.
The author is not a professional short seller. This analysis originated from noticing irregularities in publicly available information, which led to taking a short position in Alaska Air Group. Aside from this stock, 100% of investable assets are in diversified funds. However, that does make me a short-seller. Weigh that up, as you weigh up my words.



Solid investigative work here. The PIN lock logic is particularly damning because it reveals corporate awareness of session hijacking while publicly blaming users for password issues. I've seen similar patterns in fintech where companies implement workarounds that inadvertantly expose the true nature of their vulnerabilities. The fact that password changes didnt stop repeat thefts is basically case closed on the technical side.