An IT Audit of Alaska Airlines
DISCLAIMER: The author holds a short position in Alaska Air Group (ALK) and stands to profit from a decline in the share price. This report represents analysis of publicly available information, including SEC filings, public financial data, and social media documentation. It constitutes opinion, not investment advice.
The Architecture of Neglect
To understand why Alaska Airlines has failed to patch a critical vulnerability for four years, one must first look beyond the credential stuffing narrative. The reality is not that users are failing to lock their doors; it is that the building itself has no walls.
Forensic analysis of the ALK infrastructure reveals a creaking architecture - a cosmetic web skin wrapped around a decaying mainframe skeleton (Passenger Service System) likely dating back to the 1980s. The breach is not occurring at the user level (passwords); it is occurring at the structural level (session management). The platform is currently operating with a Session Bleeding vulnerability that allows unauthorised actors to bypass authentication entirely, rendering passwords - and even the new PIN safeguards - irrelevant.
The “Cyber-End-All”: Anatomy of the Failure
The core of the issue lies in the Middleware Translation Layer - the code that sits between the modern website (Atmos) and the legacy database. This layer has lost the ability to maintain “State.”
The Session Bleed (The Open Door)
The most damning evidence confirms that the system is confusing user identities in real-time. This is not a “hack” in the traditional sense; it is a caching and session integrity failure.
The Mechanism: When User A requests a page, the middleware inadvertently serves a cached session token belonging to User B.
The Implication: If a normal user can stumble into this “Ghost Session,” a malicious actor can automate it. By cycling through session tokens, attackers can inherit active, authenticated sessions without ever knowing the victim’s password.
The User Reports:
Fraud Blindness
The architecture is blind to its own data. Attackers are successfully booking high-value partner awards for new beneficiaries within 48 hours of travel.
Why this is a System Failure: A functioning fraud engine would flag “New Beneficiary + High Value + Last Minute” as a hard stop. Alaska’s legacy mainframe accepts the instruction because it cannot read the risk context from the modern web layer.
Forensic Evidence: Disproving the Password Narrative
Management’s defense relies on the claim of Credential Stuffing (users reusing weak passwords). The forensic evidence categorically disproves this. If this were a password issue, Strong Authentication procedures would stop it. They do not.
The Override of Strong Procedures
We have identified multiple accounts protected by unique, 20+ character random passwords generated by password managers - never used elsewhere - that were nonetheless compromised.
“had a long complex and random password”
“I keep a fairly extensive password management”
“have unique passwords for each of my accounts”
The Compromise of the “PIN” Lock
The mandatory PIN system, introduced as a desperate operational workaround to “air-gap” the fraud by forcing users to call a human agent, has already been breached. We are seeing reports of the PIN lock itself being bypassed or reset without the user’s consent.
“my account has gotten hacked 2x within a month! Twice I have checked my account and a random flight has been booked for the thief! Please fix this! Yes I changed my password when you guys first tried to resolve this and added a pin.”
Historical Context: The Unpatched Legacy
The specific mechanism of this failure (Session Fixation/Hijacking) is not a new or novel threat. It is a known class of vulnerability that has been documented to Alaska before as per this HackerNews post from December 2024:
“Alaska exposes other customers names, record locators, flight information, phone numbers emails, and probably more. I could have canceled or changed these people’s flights.”
The poster reported all to Alaska. 4 months later the poster noted nothing had been fixed.
The Intrusion Detection Reality
Does Alaska IT know the difference between a guessed password and a stolen session? Yes.
In any standard SIEM (Security Information and Event Management) log:
Credential Stuffing looks like: 1,000 Failed Logins → 1 Successful Login.
Session Hijacking looks like: 0 Logins → Active Traffic from New IP (Russia/China).
If Alaska is telling customers “your password was weak” while their internal logs show traffic arriving with valid tokens but no login event, they are suppressing evidence of a platform failure to shift liability.
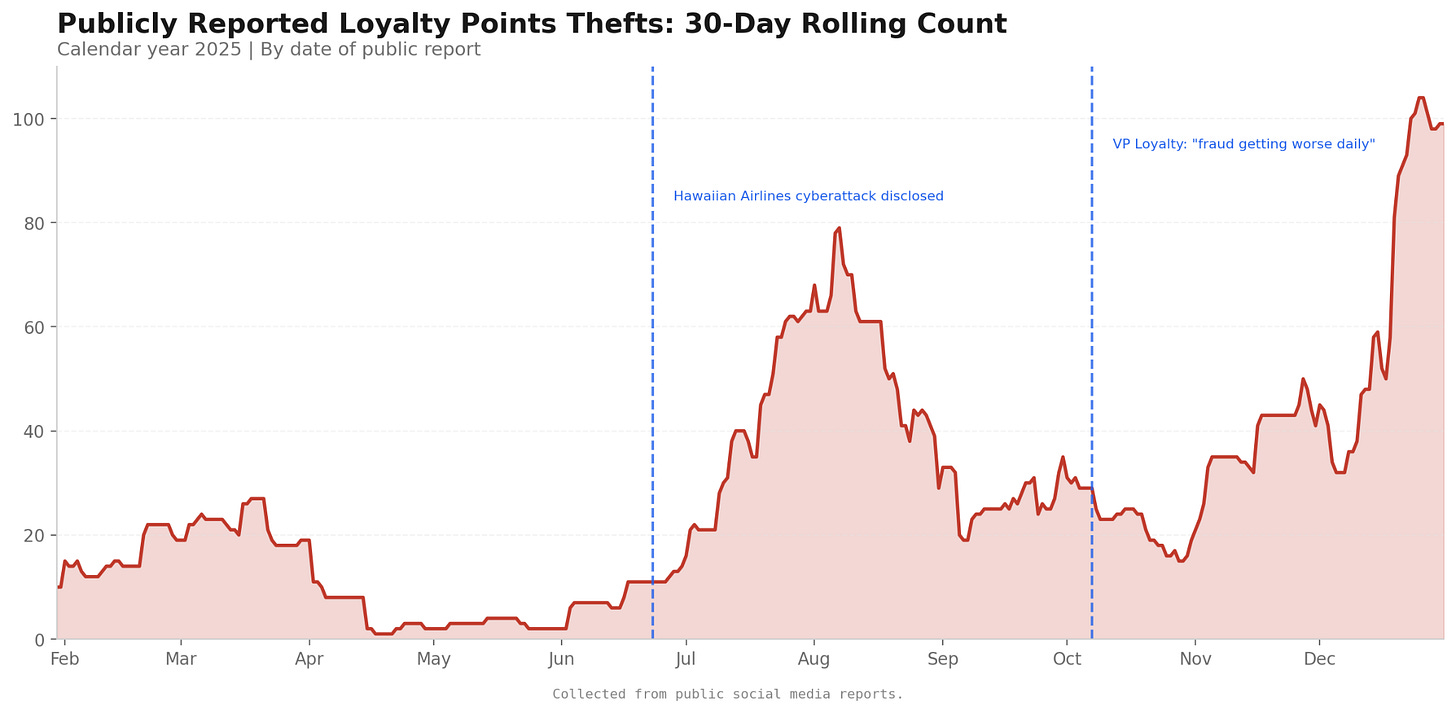
The Catalyst: The Hawaiian Airlines Merger
The acceleration of these attacks correlates directly with the 23 June 2025 Hawaiian Airlines breach. Credential stuffing compromises would show a more consistent flow of thefts.
The Combo List: The HA breach perhaps provided a fresh “High Value” target list.
The Trust Bridge: Merging the two networks possibly created a temporary “trust bridge” that allowed attackers to traverse from the compromised Hawaiian environment into the Alaska middleware, bypassing perimeter firewalls.
The Indefensible Defence: The “Dunkin’ Donuts” Standard
Alaska’s posture mirrors the Dunkin’ Donuts legal precedent. In that case, the NY Attorney General ruled that if a company knows credential attacks are bypassing their defences and fails to implement standard blocks (like CAPTCHA or 2FA), they are liable - even if the hacker used a valid password.
By implying the victims’ negligence in the process to get their miles back, Alaska is distracting the victims from the root cause.
Conclusion: The State of the Tech
Alaska’s loyalty platform is effectively a broken bank vault.
The fix is not a patch; it is a rebuild. If it were anything less, the vulnerability would have been closed in the last four years.
The faithful in the dedicated forums where I found most of the reports, frequently see the victims lambasted for their shoddy password hygiene, no matter how the victim protests.
Today, Alaska customers have no way of securing their account from theft. Any day they could find their accounts drained.
Alaska Airlines must be fully aware of this issue, yet on 4th December 2025, CFO Shane Tackett announced the preliminary results of the Accenture full IT audit.
“we don’t have a systemic architecture failure in our data or infrastructure”
One of us is mistaken.